Scope And Significance Of Data Science In Cybersecurity
Introduction:
As digital gadgets ruling the globe, a massive amount of data generating per second is unimaginable. Manipulating and handling the data by data Specialists And Data Scientist is the huge process. Processing the data and concluding the required results is vital. [1] But providing data security in the vulnerable world becomes a tedious one. As we are vulnerable in the digital era, protecting us from the vulnerabilities is cannot manageable. This blog will enhance the scope and need for Cybersecurity in the Statistical And Analytical Area.

Data Science:
The originality of data science is to handle the present and past data for future processes. Especially in business sectors, data science is used to predict customer insights, market strategies, stock details in retail shops, forecasting the organization growth. The role of a data analyst and data scientist is to analyze the problem statement and analyze the structured or unstructured data from the client, cleanse the dataset and proceed further for the requirement.
Data science in Cybersecurity slightly deviates from other business ventures. Specialized techniques are there to sort out and figure out the issues in cybercrime.
Cybersecurity:
Cyber is nothing like the copycat world of Digital. In the digital era, no one can assure 100% safety and security. The primality of Cybersecurity is to prevent malicious attacks by attackers and hackers from naïve users. [1]
The Internet is the platform and open-sources where enormous people will log in and log out every second. Internet is intermediate to transform and penetrate malicious attacks through gadgets and data available in the gadget. The evolution of cloud computing is another reason to protect the data from device and disk crashes, system failures.
Need For Data Science In Cybersecurity:
Generally, Attackers and Hackers have many intrusion and invasion techniques to enter into the user’s system or fetch the data. Those styles can be estimated and forecasted by Data scientists to prevent those kinds of attacks in the future. For instance, to provide security for confidential data in the organization, a log in username and password is mandatory. To enhance more security fingerprints, biometric sensors could be implemented.
Data scientists will analyze the attacks that have been done in the past and conclude the results relevant to the present and future-based outcomes.
Analytical Skills For Cybersecurity:
Behavioural analytics:
This technique incorporates understanding the intention of the attacker to prevent those kind of attacks. The Whitehat people provide data security for the users to analyze what kind of attack held in the past in a specified scenario. The data analyst will assist and analyze the purpose of the attack to predict similar attacks in the future. [2]
Data protection:
Here, Data Science Specialists & cybersecurity specialists have to work together to conclude and forecast the protection level. [3] It is the initial level phase, where the cyber specialist identifies how to incorporate the security levels for the system, device, websites, web applications and financial services. The data scientist will analyze the security level phases to predict the possibilities of security breaches in each phase. [4]
Associate Rule Learning:
It’s a Machine Learning Technique used by a data scientist to forecast cyber attacks. The actual responsibility of ARL is to figure out the possibilities of vulnerabilities once the website, software, application launched to the market. The ARL will figure out the third party malware and malicious bugs which intrudes into the websites or software. The data analyst or the data engineer will predict the vulnerabilities based on the threats and risks on the website. [5]
Figure 1: Encryption And Decryption Process:
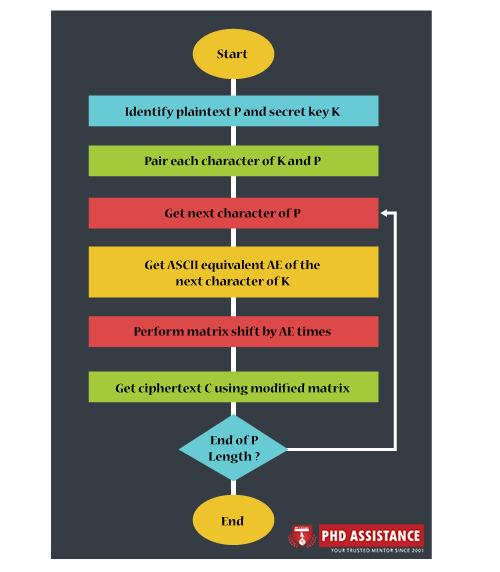
Fig1. Encryption Process
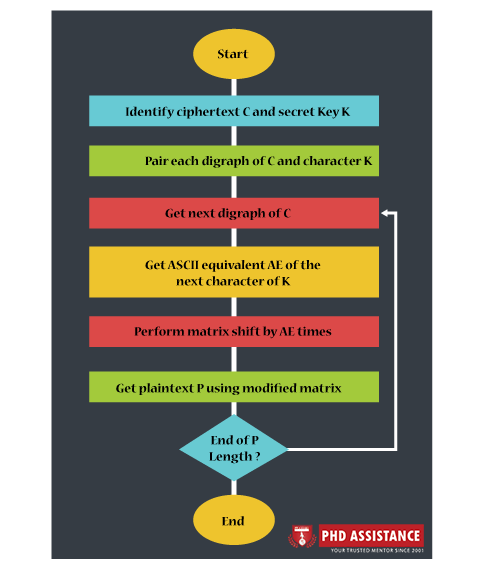
Fig2. Decryption Process
Future Scope:
- As the need for automation increases rapidly, the data beyond the process will increase. To provide protection and security for those data large number of cyber specialists are required in the future.
- Usage of legitimate applications, websites and software will be monitored by cyber specialist all the time to verify and track the details of logs. [6]
- Recent technologies such as Artificial Intelligence, Machine Learning and Cloud computing enhancing cybersecurity techniques to provide proper protection for confidential data.
Summary:
In upcoming decades, Data science and Cybersecurity plays a vital role in all domains in the world. The need for both technologies will be there wherever the Internet is available. As the need for Cybersecurity and data science is high, the scope for both technologies will be in peak.
References:
[1] Wolf, Shaya, et al. “Integrated Outreach: Increasing Engagement in Computer Science and Cybersecurity.” Education Sciences 10.12 (2020): 353.
[2] Mehta, Arvind. “Risk is a result of human behaviour: Leveraging behavioural analytics to strengthen internal controls.” Cyber Security: A Peer-Reviewed Journal (2021).
[3] Feng, Xiaohua, and Xiangrui Zhang. “Personally identifiable information security in cloud computing.” (2020).
[4] Sikos, Leslie F., and Kim-Kwang Raymond Choo, eds. Data science in cybersecurity and cyberthreat intelligence. Springer, 2020.
[5] Cains, Mariana G., et al. “Defining Cyber Security and Cyber Security Risk within a Multidisciplinary Context using Expert Elicitation.” Risk Analysis (2021).
[6] Sarker, Iqbal H. “Deep cybersecurity: a comprehensive overview from neural network and deep learning perspective.” SN Computer Science 2.3 (2021): 1-16.
 Previous Post
Previous Post Next Post
Next Post
