MACHINE LEARNING BASED INTERNET OF THINGS (IOT) SECURITY SOLUTIONS
IoT platforms have grown into a worldwide behemoth that has engulfed every element of our daily lives by expanding human life with its unaccountable smart services during the previous decade. IoT is now experiencing greater security difficulties than ever before due to easy accessibility and rapidly expanding demand for smart devices and networks. Existing security methods can be used to safeguard IoT devices. Traditional approaches, on the other hand, are ineffective in the face of advancement booms, as well as various attack types and severity levels. As a result, for next-generation IoT systems, a strong, dynamically improved, and up-to-date security system is necessary. Machine Learning (ML) has seen a significant technological development, opening up numerous new research avenues to address current and future IoT concerns. To detect assaults and identify odd behaviours of smart devices and networks, machine learning is being used as a strong technique.
INTRODUCTION
The Internet of Things (IoT) connects the electrical items to a server and exchanges data without the need for human interaction [1] -[3]. Users can access their gadgets remotely from anywhere, making them exposed to various threats. With the growing number of smart devices on the market today, the security of IoT systems is a major worry [4] -[5], as the gadgets contain private and important information about clients.
Machine learning (ML)-based algorithms offer a promising alternative for securing IoT devices. ML is a sophisticated artificial intelligence technology that requires no explicit programming and outperforms dynamic networks. Machine learning approaches can be used to educate the machine to recognise different types of attacks and provide appropriate defensive policies. The attacks can be recognised at an early stage in this situation. Furthermore, machine learning approaches appear to be promising in detecting new assaults and handling them wisely. As a result, machine learning algorithms may be able to give prospective security protocols for IoT devices, making them more dependable and accessible than before.
SECURITY OF INTERNET OF THINGS
In the twenty-first century, the security of IoT devices has become a hot topic. On the one hand, IoT pulls everything closer together and connects the entire world; on the other hand, it creates multiple entry points for various forms of attacks. Although the phrase IoT is short in context, it encompasses the entire planet with all of its smart technology and services.
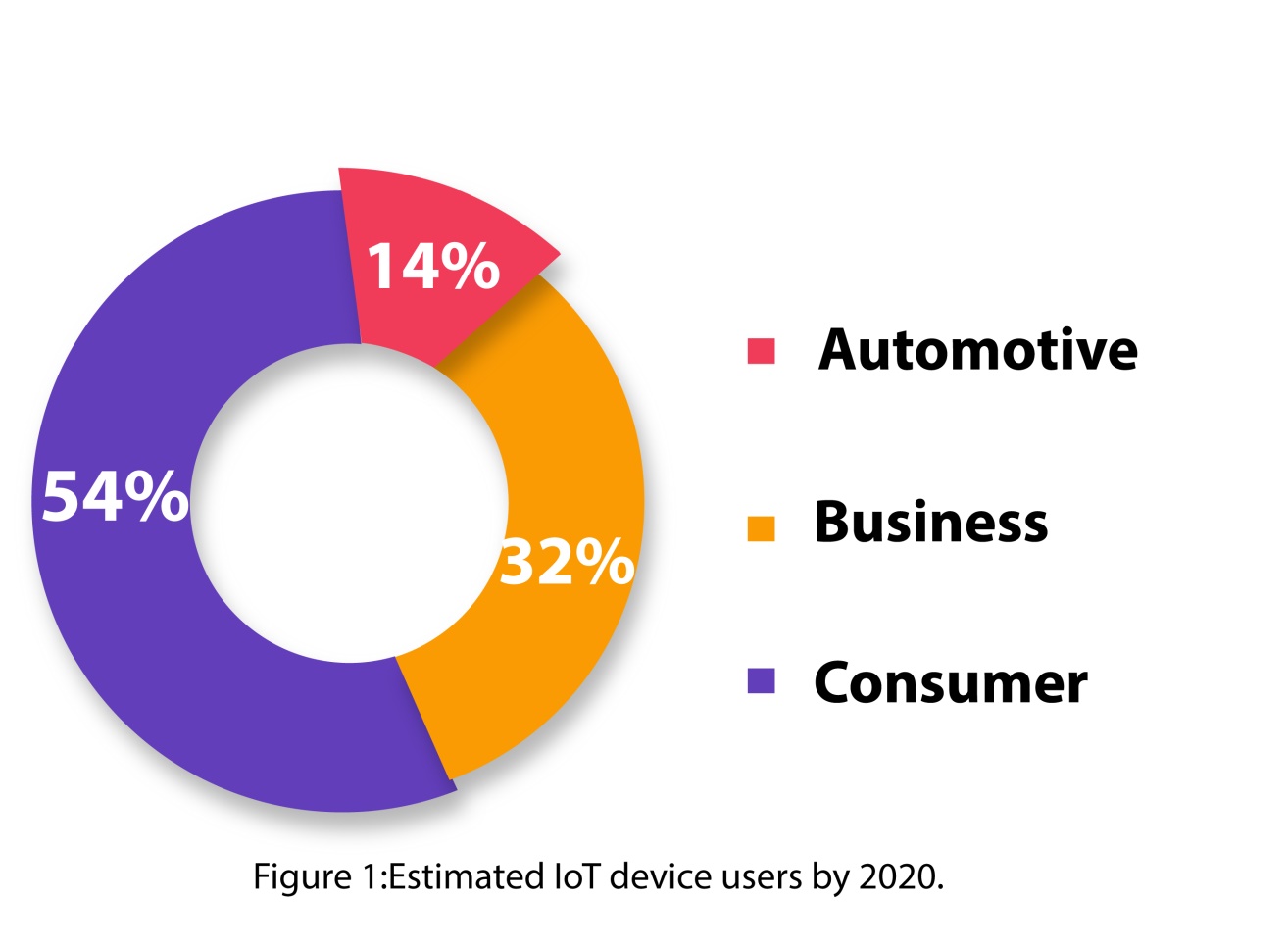
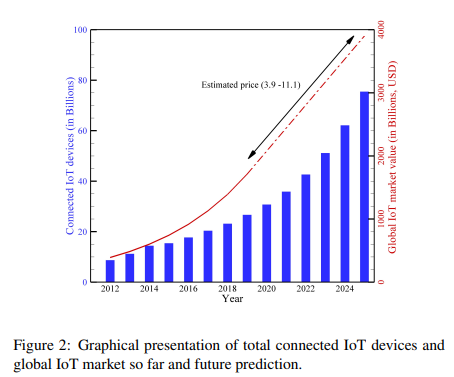
Since then, IoT has been utilised to create a link between the physical and virtual worlds by utilising various smart devices and their services via various communication protocols. With the help of IoT, what was a fantasy 25 years ago has become a reality. In a nutshell, today’s advanced world is encircled by smart technology, with IoT at its centre. People no longer have the capability to think for themselves without the use of IoT devices and services. According to a survey, by 2020, roughly 50 billion gadgets will be connected to the internet, and this number will continue to rise dramatically [6]. Figure 1[7] shows the projected percentage of IoT device users by 2020. By 2025, it is expected that IoT would have captured a market worth roughly 3.911.1 trillion dollars [14]. Figure 2 depicts the number of linked IoT devices and the global market for IoT systems to date, as well as future predictions through 2025 [8]. As a result, in the field of electrical and computer science, research on the Internet of Things, its evolution, and security has gotten a lot of attention in recent decades. PhD Assistance experts has experience in handling dissertation and assignment(SK1) in computer science research with assured 2:1 distinction. Talk to Experts Now
IOT LAYERS
The IoT architecture, which is a gateway for diverse hardware applications, was created in order to create a link and expand IoT services to every doorstep. Different communication protocols are used in different layers of IoT architecture to transmit and receive various information/data, such as Bluetooth, WiFi, RFID, narrow and wideband frequency, ZigBee, LPWAN, and IEEE 802.15. Furthermore, large-scale high-tech firms, such as Google Cloud, Samsung Artik Cloud, Microsoft Azure suite, Amazon AWS IoT, and others [9], have their own IoT platforms to service their key clients. As shown in Fig. 3, the basic IoT design comprises of three layers: perception/physical layer, network layer, and web/application layer. Hire PhD Assistance experts to develop your algorithm and coding implementation (SK3) for your Computer Science dissertation Services.
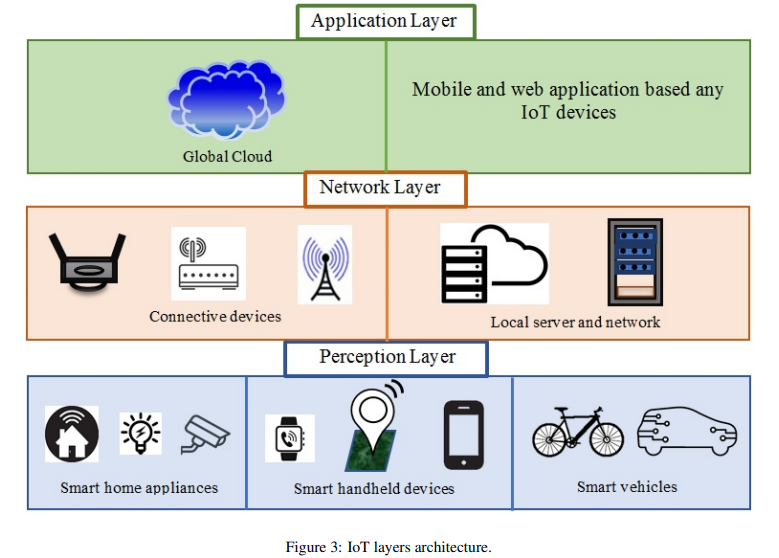
Application layer
In IoT systems, the application layer is the third layer that provides services to users via mobile and web-based software. IoT has several uses in modern technologically evolved world, based on recent developments and smart object usages. By the grace of the Internet of Things system and its uncounted services, living spaces/homes/buildings, transportation, health, education, agriculture, business/trades, energy distribution system, and so on have all become smart.
Network layer
The network layer is especially important in IoT systems since it serves as a transmission/redirecting medium for data and information using various connection protocols such as GSM, LTA, WiFi, 3-5G, IPv6, IEEE 802.15.4, and others to connect devices with smart services [10]. At the network layer, which serves as a middle-ware between the network and the next layer, local clouds and servers store and process information.
Importance of Security in IoT
Users can connect IoT devices to the internet and use them for a number of purposes, making them more accessible. On the one hand, the IoT makes human life more technologically advanced, easygoing, and conformable; on the other hand, the Internet of Things puts users’ privacy at danger due to a variety of threats and attacks [12]. Because anyone can access certain IoT devices from anywhere without the user’s permission, IoT device security has become a hot topic. To safeguard IoT devices, a variety of security systems must be applied.
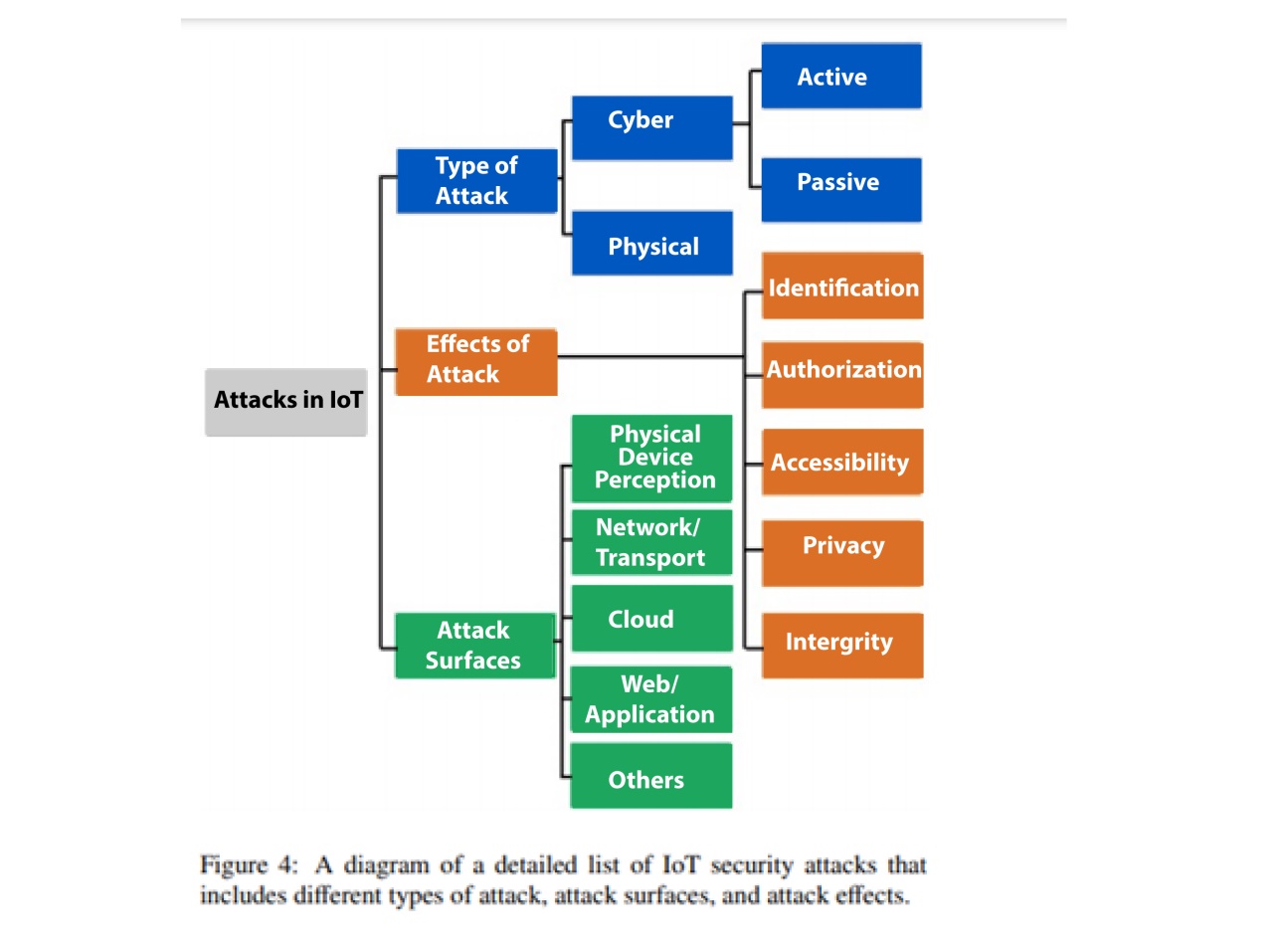
Machine Learning (ML) in IoT Security
ML is an artificial intelligence technique that educates machines using various algorithms and allows them to learn from their experiences rather than being explicitly programmed. ML does not require human intervention, does not require difficult mathematical calculations, and can operate in dynamic networks. Machine learning algorithms have made tremendous progress in IoT security in recent years [13]. As a result, by monitoring device behaviour, machine learning algorithms may be utilised to detect various IoT attacks early on. In addition, for resource-constrained IoT devices, relevant solutions can be offered utilising various ML algorithms.
RESEARCH CHALLENGES
Currently, the Internet of Things (IoT) and its relevance are gaining traction at every turn. In addition, numerous networks and application researchers have been paying attention to IoT security. The implementation of IoT, its use, and its impact on networks define many obstacles and constraints that lead to future research areas. These potential issues must be addressed in order to develop a secure and dependable IoT system. Based on previous research as well as future predictions in the IoT network, a list of prospective obstacles and future study subjects has been offered.
Data security
To protect the system, any learning algorithm requires a clear and accurate data sample from which it may be taught. In most learning techniques, different features of the available data sets are observed and used to create training data sets. In this scenario, data availability, data quality, and data authenticity are critical for training the learning methods’ dataset. Machine learning, unlike previous learning approaches, requires huge, high-quality, and readily available training data sets in order to construct an accurate ML technique. The deployment of a comprehensive and precise learning approach can be hampered if a training data set comprises low-quality data that contains noise. As a result, for effective security of the IoT network, authentication of the training data sets is a significant barrier in ML approaches [14]. To properly integrate ML algorithms in an IoT system, significant data sets are required, which are typically difficult to get dependent on the system’s ability to identify dangers and take appropriate responses. In this context, data augmentation is an important method for generating sufficient data sets from real-world data. However, in order to achieve optimum accuracy from ML algorithms, the generated new data samples must be properly dispersed in a distinct class [15].
Privacy leakage
In today’s world of IoT, privacy is the most pressing concern. People communicate data and information via smart gadgets for a variety of reasons. Client information is slowly being collected and shared in ways that the clients are unaware of. Users have no idea what, how, or where their personal information has been shared. Basic security mechanisms, such as authentication, encryption, and security updates, are included on all IoT devices. As a result, IoT devices must encrypt messages before sending them over the cloud in order to keep them private. Privacy protection, on the other hand, must be a security consideration in IoT device design requirements. Google Home Assistant (Google Home Speaker and Chromecast, for example) has exposed a user’s location. As a result, because IoT devices carry confidential and sensitive information/data, there is a risk that it will be misused if it is released.
Real-Time Update Issue
As the number of IoT devices grows, it’s more important than ever to keep track of software and firmware updates. However, keeping track of and applying upgrades to millions of IoT devices is difficult since not all devices accept air updates. In that situation, manual upgrades are required, such as real-time and data-intensive updates, which might be inconvenient for consumers at times. As a result, the phrase “lifelong learning” has been coined to describe how machines can continuously hunt for updates and strengthen their firewalls against new threats. Because IoT systems are dynamic, new apps and electronic gadgets are added to the network every day, resulting in undiscovered new assaults. As a result, adopting an intelligent and real-time updated machine learning method to detect unexpected assaults is a problem for IoT security [16], [17].
References
- Li, Xu, Rongxing Lu, Xiaohui Liang, Xuemin Shen, Jiming Chen, and Xiaodong Lin. “Smart community: an internet of things application.” IEEE Communications magazine 49, no. 11 (2011): 68-75.
- Abane, Amar, Mehammed Daoui, Samia Bouzefrane, and Paul Muhlethaler. “A Lightweight forwarding strategy for named data networking in low-end IoT.” Journal of Network and Computer Applications 148 (2019): 102445.
- Sheng, Zhengguo, Shusen Yang, Yifan Yu, Athanasios V. Vasilakos, Julie A. McCann, and Kin K. Leung. “A survey on the ietf protocol suite for the internet of things: Standards, challenges, and opportunities.” IEEE wireless communications 20, no. 6 (2013): 91-98.
- Sengupta, Jayasree, Sushmita Ruj, and Sipra Das Bit. “A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT.” Journal of Network and Computer Applications 149 (2020): 102481.
- Guan, Zhitao, Yue Zhang, Longfei Wu, Jun Wu, Jing Li, Yinglong Ma, and Jingjing Hu. “APPA: An anonymous and privacy preserving data aggregation scheme for fog-enhanced IoT.” Journal of Network and Computer Applications 125 (2019): 82-92.
- da Cruz, Mauro AA, Joel JPC Rodrigues, Arun Kumar Sangaiah, Jalal Al-Muhtadi, and Valery Korotaev. “Performance evaluation of IoT middleware.” Journal of Network and Computer Applications 109 (2018): 53-65.
- Statista, ”Internet of Things to Hit the Mainstream by 2020” https://www.statista.com/chart/2936/internet-of-things-tohit-the-mainstream-by-2020/, 2019.
- Surya, Lakshmisri. “IoT Security Techniques Based On Machine Learning: How IoT Devices use AI to Enhance Security.” International Journal of Computer Trends and Technology (IJCTT)-Volume 67 (2019).
- Chaabouni, Nadia, Mohamed Mosbah, Akka Zemmari, Cyrille Sauvignac, and Parvez Faruki. “Network intrusion detection for IoT security based on learning techniques.” IEEE Communications Surveys & Tutorials 21, no. 3 (2019): 2671-2701.
- Amendola, R. Lodato, S. Manzari, C. Occhiuzzi, and G. Marrocco, ”RFID technology for IoT-based personal healthcare in smart spaces,” IEEE Internet of things journal, vol. 1, no. 2, pp. 144-152, 2014.
- Camara, P. Peris-Lopez, and J. E. Tapiador, ”Security and privacy issues in implantable medical devices: A comprehensive survey,” Journal of biomedical informatics, vol. 55, pp. 272-289, 2015.
- Singh, A. Payal, S. Bharti, A walkthrough of the emerging IoT paradigm: Visualizing inside functionalities, key features, and open issues, Journal of Network and Computer Applications, vol. 143, pp. 111151, 2019.
- A. Razzaque, M. Milojevic-Jevric, A. Palade, and S. Clarke, ”Middleware for internet of things: a survey,” IEEE Internet of Things Journal, vol. 3, no. 1, pp. 70-95, 2016.
- Sezer, Omer Berat, Erdogan Dogdu, and Ahmet Murat Ozbayoglu. “Context-aware computing, learning, and big data in internet of things: a survey.” IEEE Internet of Things Journal 5, no. 1 (2017): 1-27..
- Makhdoom, M. Abolhasan, J. Lipman, R. P. Liu and W. Ni, ”Anatomy of Threats to The Internet of Things,” in IEEE Communications Surveys & Tutorials. doi: 10.1109/COMST.2018.2874978
- I. Jordan and T. M. Mitchell, ”Machine learning: Trends, perspectives, and prospects,” Science, vol. 349, no. 6245, pp. 255- 260, 2015
- F. Nweke, Y. W. Teh, M. A. Al-garadi, and U. R. Alo, ”Deep Learning Algorithms for Human Activity Recognition using Mobile and Wearable Sensor Networks: State of the Art and Research Challenges,” Expert Systems with Applications, 2018.
- T. Um et al., ”Data augmentation of wearable sensor data for parkinsons disease monitoring using convolutional neural networks,” in Proceedings of the 19th ACM International Conference on Multimodal Interaction, 2017, pp. 216-220: ACM
- Suthaharan, ”Big data classification: Problems and challenges in network intrusion prediction with machine learning,” ACM SIGMETRICS Performance Evaluation Review, vol. 41, no. 4, pp. 70-73, 2014.
- Chegini, Hossein, Ranesh Kumar Naha, Aniket Mahanti, and Parimala Thulasiraman. “Process Automation in an IoT–Fog–Cloud Ecosystem: A Survey and Taxonomy.” IoT 2, no. 1 (2021): 92-118.
 Previous Post
Previous Post
